How MEV and Flashbots Shape the Dark Side of Private Transactions
Introduction
Private transactions emerged from the worlds of MEV (Maximal Extractable Value). While there are a few providers that allow transactions to be included in a block without going through the mempool, Flashbots is the most widely used. Today, private transactions have become hackers' primary way of executing attacks. In this blog post, we will look into how MEV and Flashbots evolved and how it is used in high-value and illicit transactions today.
The Evolution of MEV
In blockchain’s early days, there was no MEV due to the limited functionality of Bitcoin and its various forks. However, the creation of Ethereum, a Turing complete blockchain, introduced a new paradigm where transaction placement became meaningful and potentially profitable.
While it isn’t clear when MEV started precisely, it became popular with the publishing of the Flashboys 2.0 paper, where the term MEV was coined. Another source that called out the dangers of MEV was the Ethereum is a Dark Forest blog post. In this post, Dan Robinson was among the first to point out the illicit activities happening in the mempool and the centralizing forces beginning to form.
The surge in MEV activities led to network congestion and gas wars, creating a negative experience for the average user. To counter this, Flashbots developed MEV-Geth, a patched Geth client. This allowed anyone to submit transaction bundles to miners, boosting transparency and fairness. Despite initial criticism, it's now widely accepted that MEV can only be minimized, not completely eradicated.
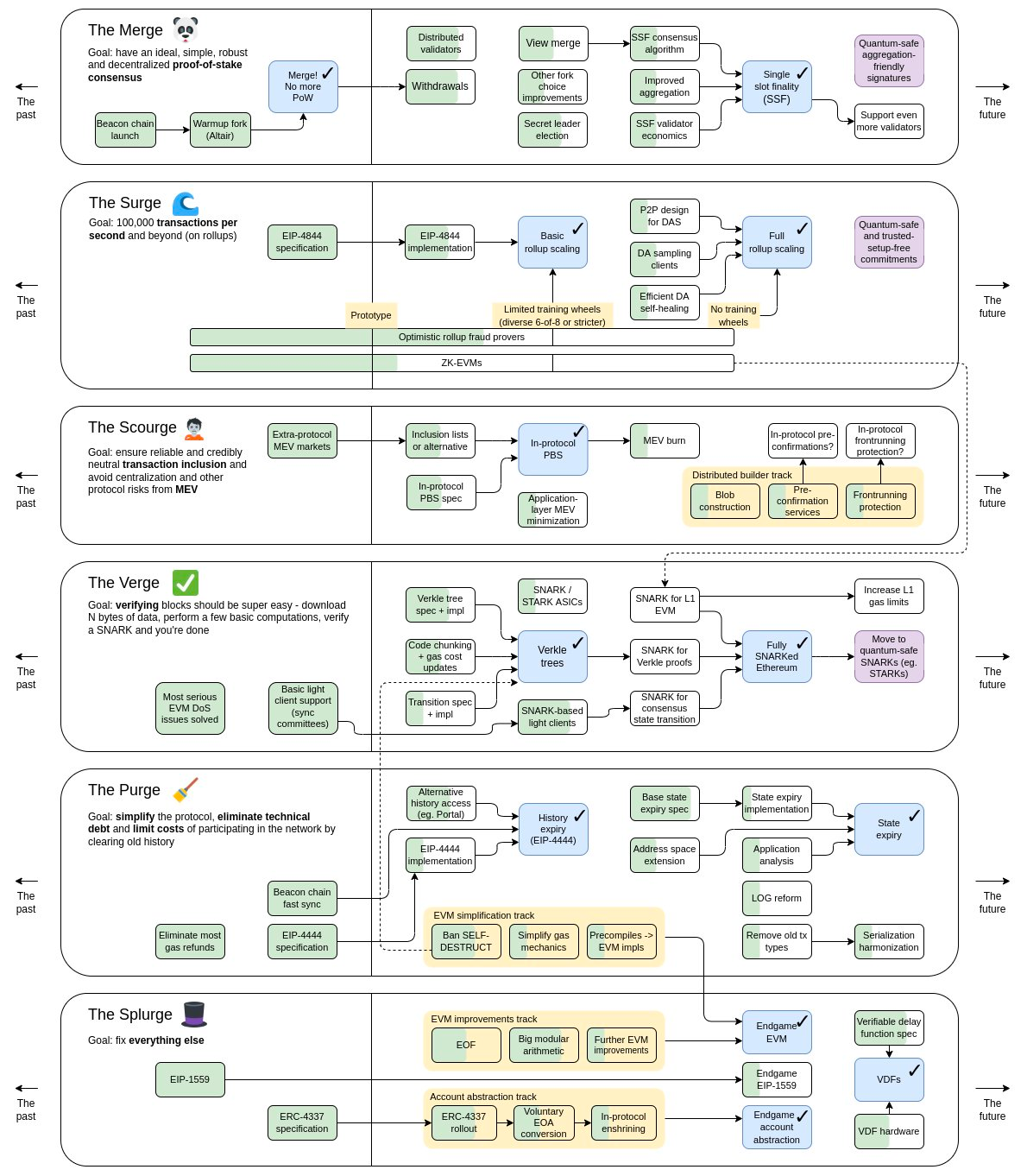
The importance of combatting MEV is front and center today and is even a core part of Vitalik’s Ethereum Roadmap - in the section nicknamed the Scourge, which focused on ensuring reliable and fair credibly neutral transaction inclusion, solving MEV issues:
Proposer Builder Separation (PBS)
The transition from proof of work (PoW) to proof of stake (PoS) in the Ethereum blockchain introduced new challenges. To address the disparity between home stakers and sophisticated actors, Flashbots proposed the concept of Proposer Builder Separation (PBS). Under PBS, the responsibility of proposing a block and building it is separated. This separation involves several key players:
Proposers (Validators): Responsible for running the consensus and execution clients and proposing a block whenever they are chosen to propose a block.
Relays: They have several responsibilities, primarily ensuring that the proposer receives valid blocks and preventing direct communication between builders and proposers to ensure decentralization.
Builders: Highly skilled teams who utilize powerful hardware, sophisticated statistical techniques, and modeling to construct the most lucrative block possible.
Searchers: Sophisticated actors who constantly race to find profitable opportunities. They submit profitable bundles to the builders via relays.
Today PBS is implemented by an opt-in service called MEV-Boost that validators choose to run to get MEV blocks. As part of the Ethereum roadmap, the role of the relayer is expected to be integrated into the Ethereum protocol. This integration aims to address centralization concerns and potential vulnerabilities.
MEV in practice
MEV, or Maximum Extractable Value, encapsulates the various actions actors can undertake to generate profits. These can be categorized broadly as follows:
Arbitrage: Actors capitalize on price discrepancies across decentralized exchanges (DEXs). This activity benefits regular users by ensuring price parity across various DEXs.
Front Running: When a profitable transaction is discovered, actors race to be the first to exploit it.
Back Running: Actors aim to be the first transaction right after another lucrative one, often involving a price oracle update.
Liquidation: Bots liquidate borrowers' collateral on lending protocols for a commission. While it is painful for the borrower, this activity is by design and ensures the ecosystem is healthy.
Sandwiching: When a user initiates a transaction with high slippage, an actor can take advantage by sandwiching the user's transaction with their own.
Hacking: This involves exploiting vulnerabilities to make a profit, often to the detriment of other users.
Flashbots empowers Searchers to better capture these opportunities by enabling:
Privacy: Enables actors to bypass the mempool, thus negating the risk of their transaction being copied and front run by a bot.
Placement: Allowing searchers to decide the sequence of transactions they are interested in - this is enabled by submitting bundles. This is crucial for most types of MEV activities.
Flashbots, true to their mission, provide several outlets to provide visibility into the activity of the Flashbots network. Some examples are:
All transactions in the following examples were verified using Flashbots API.
Liquidator
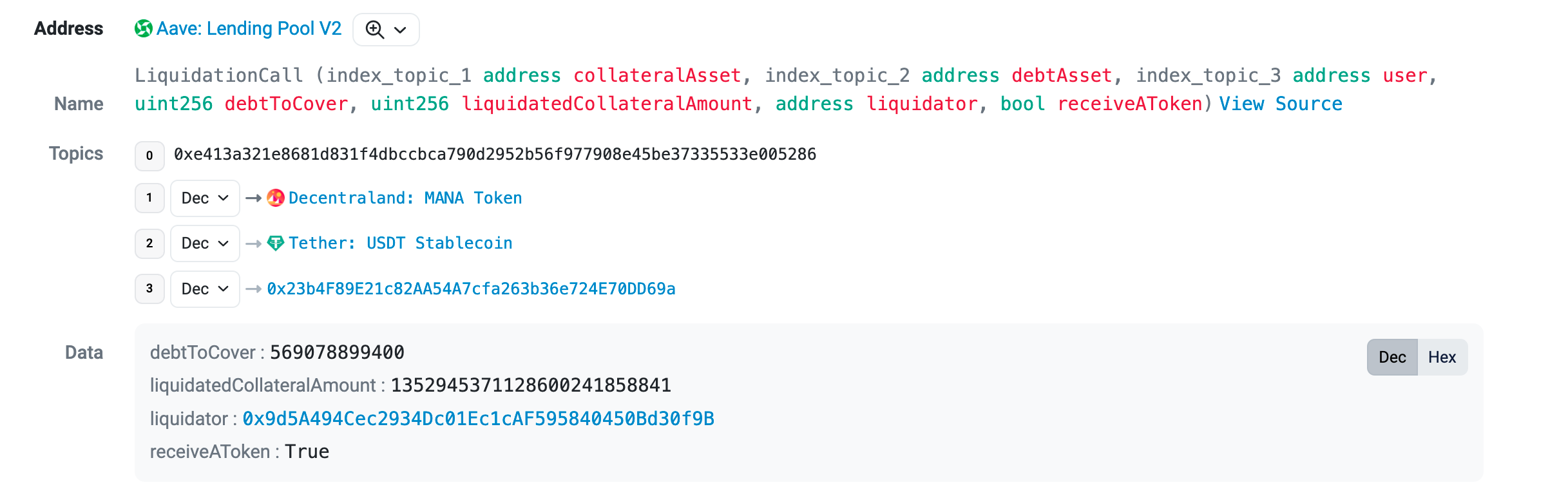
In this case, the searcher liquidated a massive AAVE debt position amounting to $610,730. To guarantee that the liquidation transaction won’t get front-run the searcher used Flashbots to ensure the transaction was executed at the beginning of the block, specifically at index 1 (as blocks execute in reverse order).
Despite the scale of the liquidation, it did not yield a profit for the searcher. The reason is, as the potential gain increases, more bots submit bundles to the Flashbots network. Therefore, to secure the acceptance of their bundle, searchers must propose a larger reward to the block builder, eventually leading to a situation where the majority of profits are directed to the validator.
Sandwich Attacks
In this example, an attacker sandwiched not only one but two victims trying to buy memecoins on Uniswap V2 DEX, making $31,524 in profits. The attacker used Flashbots to ensure that his transactions sandwiched both victims.
Front Run Transaction: <br/> https://etherscan.io/tx/0x254d8d0f857ca85dd7b38731c0c6bf8b09fb1bfc29e362f9f2b6251b5d329da5 <br/> Index 1 in the block
Victim 1: <br/> https://etherscan.io/tx/0xc0505eb5777383a78d127dcd60077eaaba3af3e16239586cda1c4ef70825e099 <br/> Index 2 in the block
Victim 2: <br/> https://etherscan.io/tx/0x01a3108d52726cbb324a935c083427e567f7e908c76daa21700bbdaa4477a466 <br/> Index 3 in the block
Back Run Transaction: <br/> https://etherscan.io/tx/0x69652dfa44cbaa27f9fbb4950c25198a700c2351e7f8a5028998bd49194e1814 <br/> Index 4 in the block
Source: Sandwich transaction detail: 0x6bfb989c7405cd0ea38a204e11ee08f1a538c2e976262cee092f0886061a722b
Hacks
Private Transaction in the Nomad Hack On Aug 1st, 2022, the Nomad bridge, a cross-chain bridge between several blockchains, was exploited, and approximately $190M in assets were stolen. See our previous blog post for a more in-depth breakdown of the attack: Combating Bridge Attacks: A Closer Look at the Attackers’ Preparations | Redefine: DeFi Risk Assessment and Mitigation for Investors
The attacker submitted his transactions to the network using Flashbots.
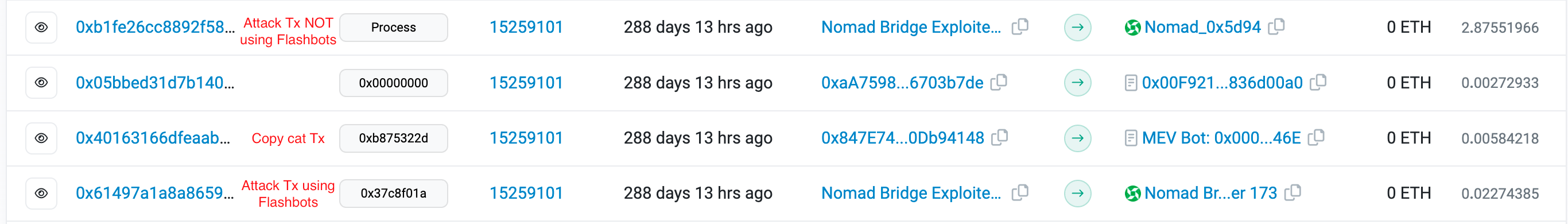
This is a screenshot of the first transactions in the block in which the attack was executed:
As can be seen in the response from the Flashbots API:
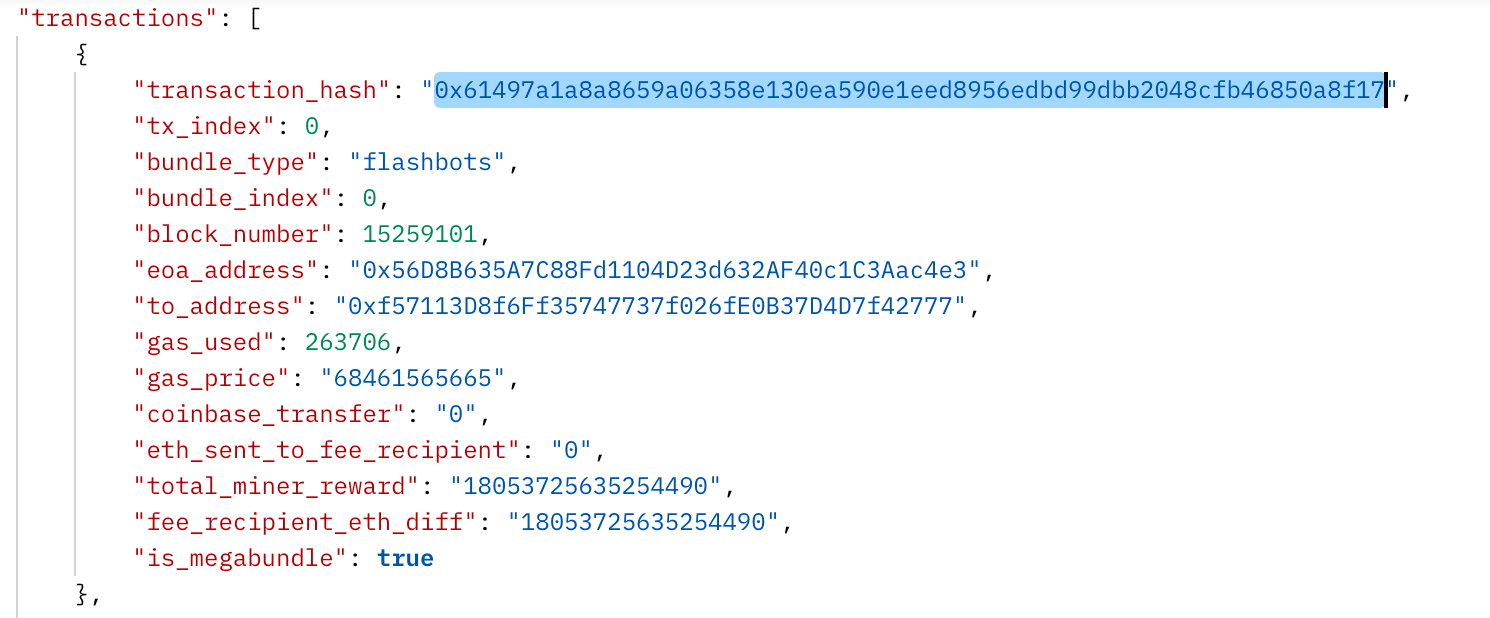
Only the first three transactions in the block used Flashbots.
As can be seen, the very first transaction is the attackers using Flashbots to profit 100 WBTC from the Nomad contract.
The Following attack seems to already be an MEV bot that appears to have copied the attack and also uses Flashbots to profit 100 WBTC.
The fourth transaction is the attackers, this time not using Flashbots. One might assume that this tipped off the MEV bot and allowed it to copy the attack.
In the next block, there are already copy cats copy pasting the attack data payload and profiting from the attack:
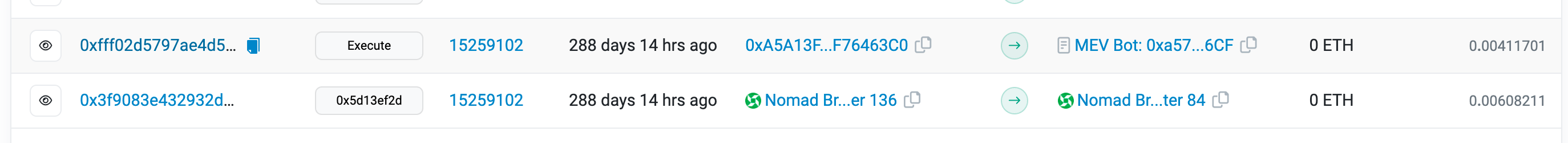
88% of addresses conducting the exploits were identified as copycats. Together, they stole about $88M in tokens from the bridge.
This attack demonstrates the importance of attackers to executing their attacks using Flashbots. Otherwise, MEV bots can easily copy the attack payload and beat the hackers to it.
Fei Rari Hack
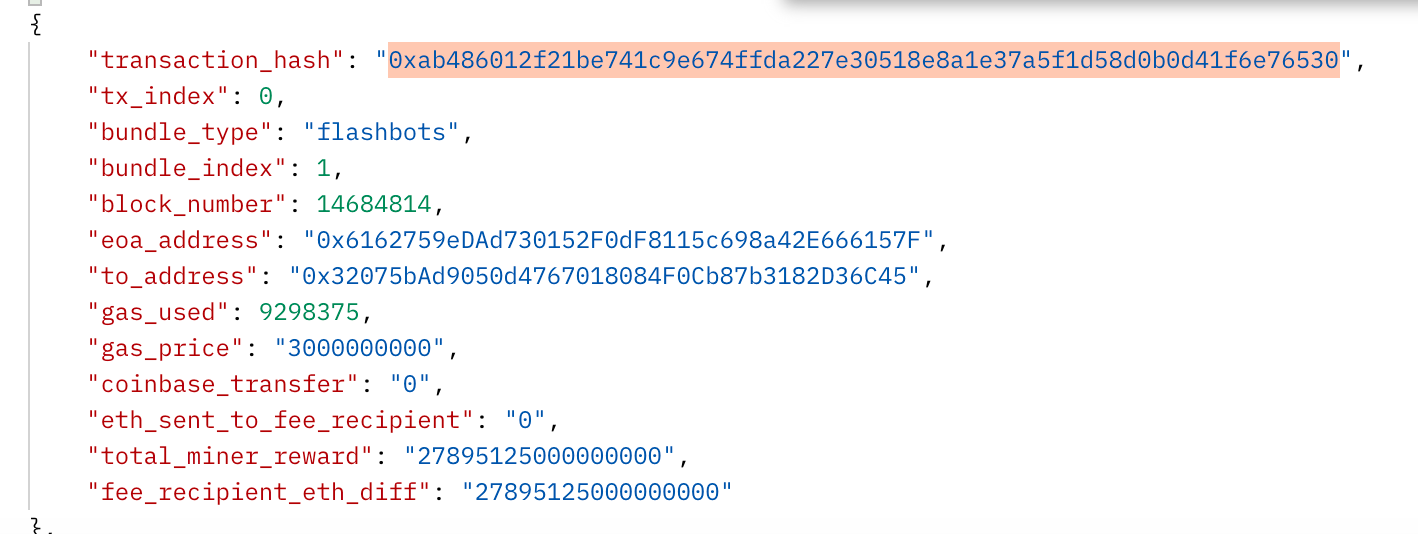
An attacker exploited a vulnerability in Rari Capital's protocol, which did not correctly record borrowed assets before allowing the withdrawal of collateral. Using flashloans, the attacker borrowed ETH, withdrew their collateral, and kept the borrowed ETH, repeating this process for multiple tokens. The attack resulted in a loss of around $79.7 million.
https://etherscan.io/tx/0xab486012f21be741c9e674ffda227e30518e8a1e37a5f1d58d0b0d41f6e76530
This attacker also used Flashbots to execute the attack:
Team hack
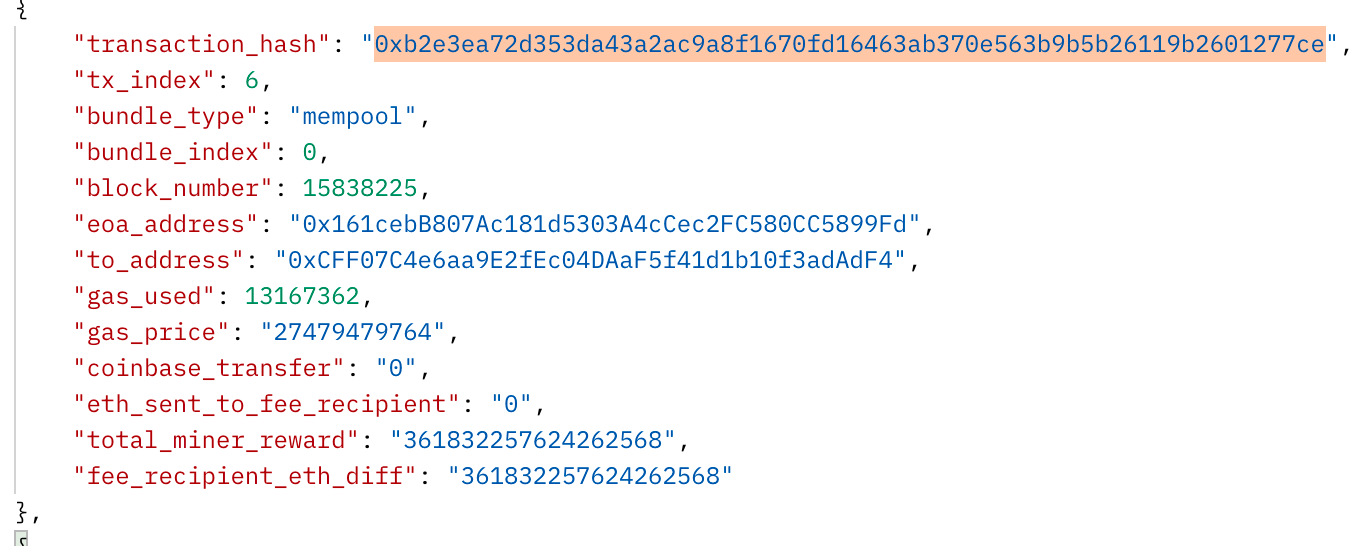
Team Finance, a project that claims to specialize in project security and automation, was hit by an attack due to a vulnerability in their smart contracts. This exploit allowed an attacker to transfer locked assets from Uniswap v2 to a manipulated Uniswap v3 pair, resulting in significant profits for the attacker. The attack caused a loss of $15.8 million, severely impacting several pools.
https://blocks.flashbots.net/v1/blocks?block_number=15838225
As can be seen, in this case, the attacker also used Flashbots to execute his attack.
https://etherscan.io/tx/0xb2e3ea72d353da43a2ac9a8f1670fd16463ab370e563b9b5b26119b2601277ce
Conclusion
This blog post delves into the development of MEV and the Flashbots network, providing a sense of the problem's magnitude while exploring the impressive solutions developed by Flashbots and the Ethereum Foundation to better align incentives and mitigate the unwanted side effects of MEV.
To protect oneself from different types of MEV, it's crucial to understand them. For instance, when trading on a DEX, setting the slippage low and minimizing the price impact is essential. Exploring solutions like Flashbots' private transactions can also protect against being sandwiched. For more information, check out https://docs.flashbots.net/flashbots-protect/overview.
It's also essential for security solutions to recognize that they may not always have enough time to identify a pending attack, especially if it's submitted through Flashbots. Finally, DeFi platforms should take MEV into account when building applications to minimize MEV leakage.
,