Understanding Mint and Burn Functions: Risks and Protective Solutions Mint function and its risks
Mint function and its risks
In this post, we will explore the mint() and burn() functions, their objectives, associated risks, and how Redefine can safeguard its customers from these.
(Not too) Technical background
The ABI (Application Binary Interface) of a smart contract is an interface that defines how other contracts or external applications can interact with the contract. It includes the function names, input and output parameters, and their data types.
The functionality of a smart contract refers to the execution of code within the contract. This code is stored as bytecode and executed by the EVM (Ethereum Virtual Machine).
Think of it as a restaurant where the ABI is the menu, listing available dishes, descriptions, and prices, while the bytecode is the kitchen, executing the desired functions and logic based on the customers’ choices.
The Importance of Mint and Burn in Tokenomics:
Mint and burn are the equivalents of quantitative easing/tightening in traditional finance.
Minting refers to creating new tokens and adding them to the circulating supply. When there are more tokens, assuming the demand stays constant, the increase in supply could lead to a decrease in the token's price.
The opposing action is burn, which removes tokens from the circulating supply. The financial impact is the opposite of minting and leads to a price increase, once again, assuming the demand remains constant.
These functions are very common in tokens, and can be considered as a critical feature required to control their tokenomics. Nevertheless, when these functions are unprotected one accidental or ill-intentioned call is all it takes to destroy a token's value. Let’s go through two examples of unprotected mint() functions:
1. The owner can mint an unlimited supply:
Although this practice is commonly seen in token contracts, it introduces an attack vector that could result in wiping the token's value. In this scenario, one actor could maliciously mint an unlimited amount of tokens to his wallet, sell them, or use them for market manipulation and as a result, massively decrease the token's price. For example, In 2021, Levyathan.finance suffered an attack where a malicious actor accessed a wallet's private keys on GitHub. The wallet had unlimited minting permissions, enabling the attacker to mint and dump 100,000,000,000,000,000,000,000,000 LEV tokens which led to a price drop to nearly 0, causing a $1.5 million loss.
2. Anyone can mint an unlimited supply:
This is a rare and much more dangerous occurrence than the previous one. It means that anyone can call the mint() function and increase the total circulating supply of a token, which leads to a significant price drop. For example, let’s take this code snippet:
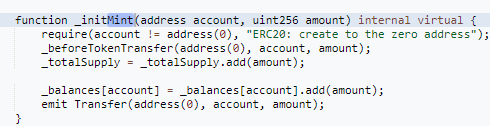
We can see that the _initMint () function is callable by any address except for the zero address. In the second part of this code, we can see that by calling this function, both the caller balance and the token’s total supply will increase, a behavior that could lead to a significant decrease in the token's price.
There is another example of this case in a decompiled unverified contract, which means that only it’s bytecode is visible, with no ABI nor available source code:
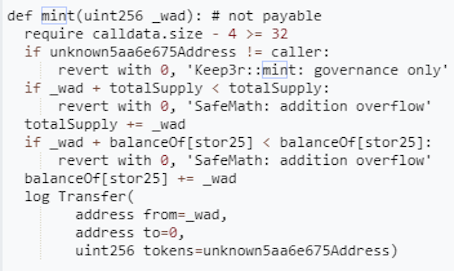
By calling this function, anyone can inflate the token's total supply as they wish, with no limits, Which can lead to a decrease in the token price.
Redefine's symbolic execution engine provides an additional layer of security by detecting potential vulnerabilities in the mint() and burn() functions. As part of our analysis, Wev'e analyzed tens of thousands of tokens that were listed on Uniswap. During this process, we identified a troublesome inactive token, which was implemented by a well-known dApp. The dApp quickly addressed the issue following our detection.
We examine the bytecode of each contract and determine potential execution paths. By simulating various inputs and outputs, we can precisely identify security flaws. When our engine detects a suspicious token, it replicates the call on a local fork, allowing us to track changes in the total supply that might signal a security vulnerability. Since our solution runs on the bytecode, it can bypass obstacles such as misleading function names or unverified contracts. Using this process, we can automatically identify potential issues with any function that unreasonably affects the total supply, like unbounded mint calls, and promptly warn users about potentially risky tokens. By using our symbolic execution engine, we can provide a safer and more secure environment for our users to transact with confidence.
Conclusion:
As we know, the beauty of DeFi comes with multiple risks, understanding the risks associated with functions that affect the total supply of a token could make us all a bit safer. Redefine’s security solutions protect users by detecting and mitigating potential vulnerabilities, providing a more secure and safer way to interact on-chain. Want to learn more about our solutions? Book a demo
,