Understanding Price Oracle Manipulation
DeFi strives to revolutionize financial services. One of the main risks facing DeFi is cyberattacks that aim to steal funds invested in DeFi platforms. The most common DeFi hack is oracle manipulation. Many platforms that fell victim to this attack including yEarn, Harvest, xToken, bZx, Cheese Bank, Synthetix.
What are Oracles?
Smart contracts are great at executing predetermined code but weak in interfacing with the outside world. They are only exposed to on-chain information. Developers use oracles to solve this problem. Oracles are protocols that transmit information from outside the blockchain and add it on-chain to update smart contracts. Uploading information on-chain is essential for creating decentralized platforms with real-world use cases. For example, lending platforms need up-to-date asset prices to know if a borrower is under-collateralized and needs to be liquidated (for more information on DeFi lending platforms, see our DeFi Guide). The Augur platform provides another use case, which allows users to bet on the outcomes of real-world activities – like election results. Oracles upload the results to smart contracts, which settle them accordingly.
The main challenge with oracles is ensuring that they are sufficiently decentralized to prevent malicious actors from uploading false information. To achieve a satisfactory level of decentralization projects like Chainlink and Band use a structure that incentivizes participants to upload true information and penalizes them for uploading false information. Some projects, like Maker, emphasize oracle decentralization and aggregate many different price feeds. The Maker oracle aggregates on-chain price feeds as well as off-chain price feeds from CEXs (Centralized Exchanges). The average between them is then taken. The Maker oracle discards any price feed that deviates more than 1% from the aggregated average. This level of decentralization makes an oracle attack on the platform extremely difficult. (for more information regarding the Maker oracle click here).
Other DeFi projects don’t emphasize decentralization as much and rely instead on on-chain information from a single DEX to get a price feed (see DeFi Guide for more details on DEXs). The standard method attackers use to manipulate the price of an asset listed on a DEX is by using a flash loan to change its price artificially.
What is a Flash Loan?
A flash loan is a financial instrument unique to crypto enabled by the use of smart contracts. Flash loans allow users to borrow almost infinite sums of money without collateral for the duration of one block. The flash loan supplier requires the borrower to return the loan inside the same block. If the borrower fails to do this, then the transaction reverts, and the money returns to the borrower – hence flash loans are risk-free for the lender. Flash loans are beneficial when arbitraging and are essential in improving DeFi’s price efficiency. On the flip side, hackers can also use flash loans to exploit weaknesses and inflict huge financial damages in a short time frame. (for more information).
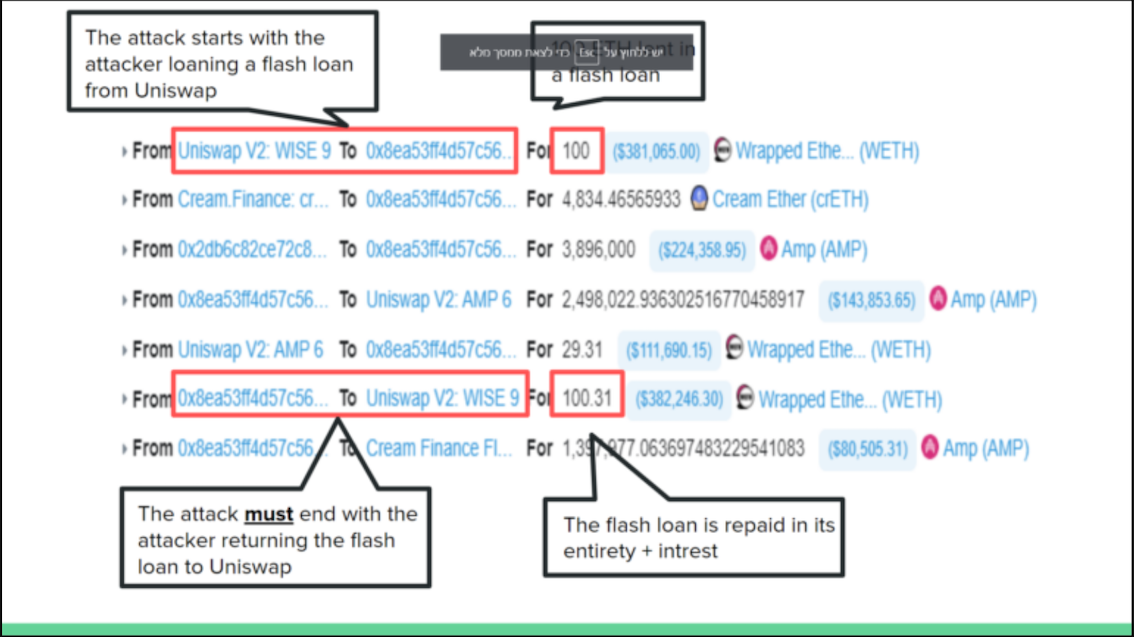 An example of a flash
loan attack on the CREAM protocol
An example of a flash
loan attack on the CREAM protocol
Oracle Manipulation and Profiting
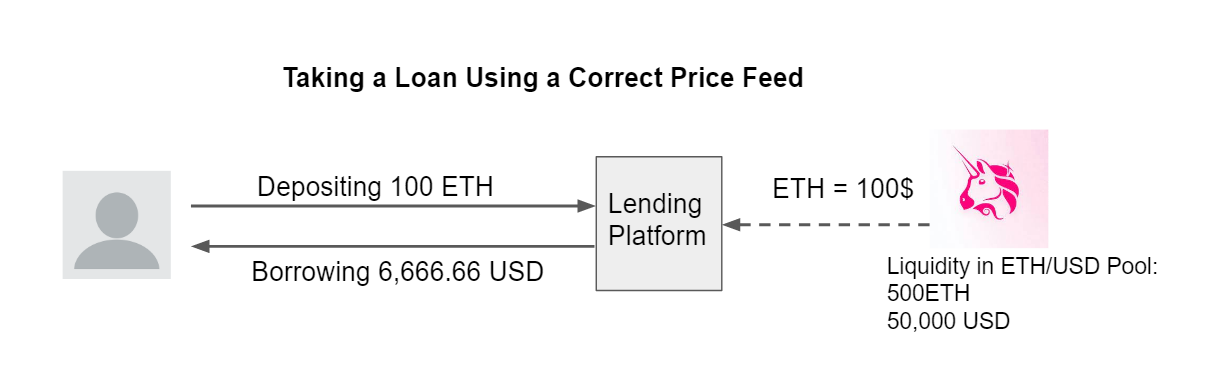
Lending platforms require borrowers to have a collateralization ratio of 150%, which means that for every 1 USD loaned there needs to be 1.5 USD locked on the platform as collateral.
For example, a user that deposits 100 ETH as collateral can loan up to 6,666 USD, assuming that the price of 1 ETH is 100 USD.
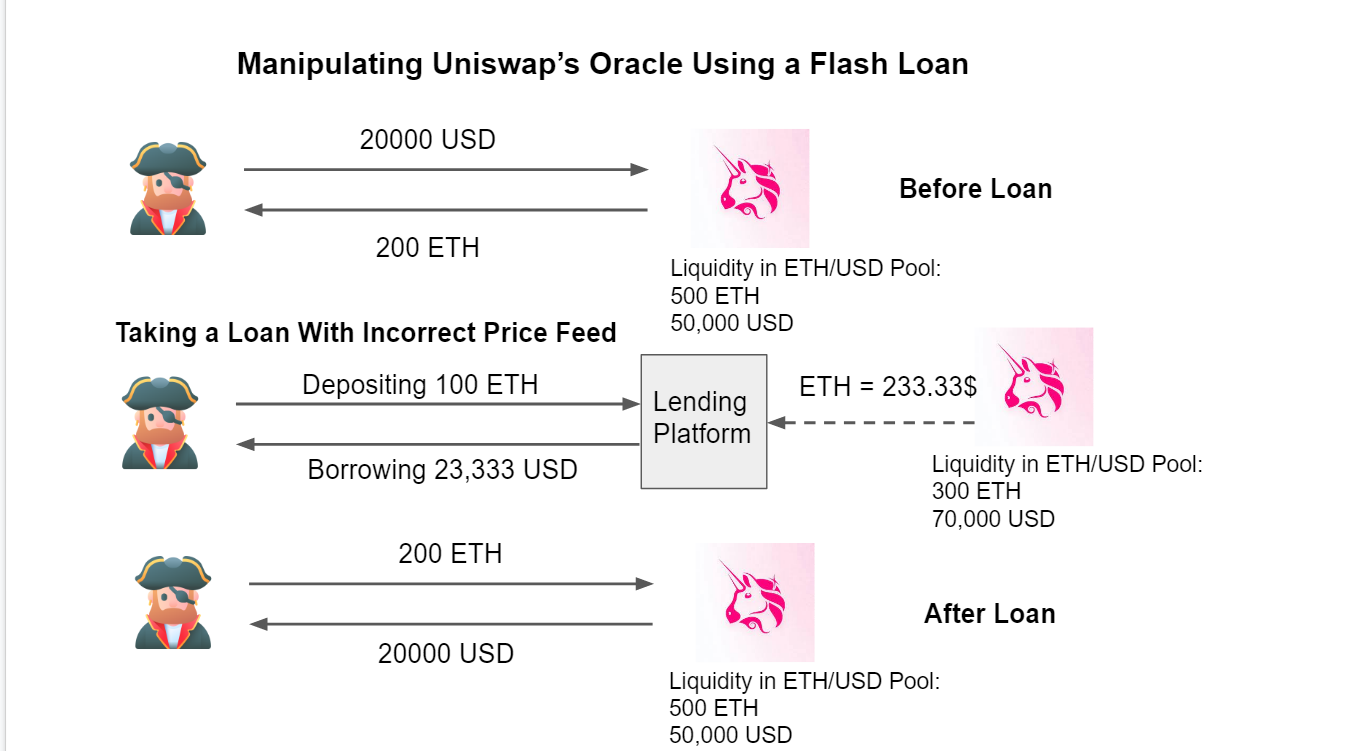
An example of a price oracle attack is when an attacker wants to steal funds from a lending platform that relies on a Uniswap oracle. The attacker loans 20,000 USD using a flash loan and then trades 20,000 USD for 200 ETH on a Uniswap ETH/USD pool – assuming 100 USD per ETH.
The Uniswap exchange now calculates the price of ETH to be 233.33 USD. Previously, a user depositing 100 ETH could borrow 6,666.66 USD. The distortion of the price oracle makes it so that the same 100 ETH can now borrow 15,555 USD.
Prevention
The best way to enhance platforms security is by using the service of a robust decentralized oracle such as Chainlink or by aggregating many different price feeds. If a platform decides to simply use an on-chain oracle, then there are a few precautionary measures available to improve platform security. They should use oracles based on pools with deep liquidity so that an attacker will be hard-pressed to skew the prices enough for an attack to be worthwhile. Another way to prevent a flash loan attack is to add a slight delay in the steps required to interact with the platform. This slight delay prevents flash loan attacks because they are required to start and finish in the same block. While this measure might limit composability and user experience, it is an effective solution.
Conclusion
Price oracle manipulation is the most common attack method in DeFi today. This is primarily because there is almost no monetary downside for the attacker. If the attack fails, the only cost is the transaction fees. If the attack succeeds, the upside is extremely lucrative.
Some blame flash-loans and call for platforms to stop supplying them. I believe that these attacks have a cleansing effect, requiring developers to strive for even more security and emphasize oracle decentralization. As DeFi evolves and developer teams gain more experience it is to be expected that platforms will become more secure and oracle attacks will become less common.
,